Observed every October, the annual Cybersecurity Awareness Month is committed to encouraging personal accountability, secure behaviors, and maintaining digital privacy in the cybersecurity landscape. This initiative was created as a joint effort between government and industry, providing resources to stay safe and secure online.
This October we are focusing on good security habits.
Thank you. We hope you had some fun while learning something new about cybersecurity and ways to stay secure.
Some parting tips on being safe online, pausing before clicking, and being thoughtful about cybersecurity.
...
Human Error vs Sound Judgment?
...
Slow down and pause before you act. Human Error has been identified as the leading reason for most security incidents. Watch this Mimecast sketch and see where Human Error should be replaced with Sound Judgment. After watching, see if you can reduce Human Error in your day-to-day activities.
A last lesson from the 1950s about being "thoughtful". What does that mean? Well, watch this video and find out why from “Billy” (StaySafeOnline.org)
Some key points to remember:
Use sound judgment and avoid human errors. Slow down and pause before clicking. Updating to the latest security software, web browser, and operating systems. Understand at least the basic security settings for all your apps and devices. (Mimecast Human Error vs Sound Judgment)
Be aware of Deepfakes and always verify using separate channels, such as using known contact information or official websites. (Deepfake AI)
Create strong, unique passphrases, and do not Re-Use those passwords. Change default passwords for all your devices. (Magic passwords - The Secret)
Be aware and on the lookout for phishy things. (Phishing It Wasn't Me)
DO Know your data. Use added caution to protect data that is sensitive, whether it on paper or digital.
- Pay attention to opening email links or attachments. Make sure it was something you expected, and you know who sent it.
- Be careful not to provide/give away sensitive data. Don't be fooled. Always confirm who you are sending the data to, and it is someone who should be receiving the sensitive data.
Avoid using weak passwords or storing passwords in unreliable places; Such as plain text (word, excel, email, phone, google) or even on sticky notes on the office desk or around the house.
- Use Multifactor for all services that you have access to. (i.e. bank login, personal email, social media, personal cloud storage, etc.)
- Encrypt sensitive data whenever possible. Understand how to encrypt or protect sensitive data.
- Back up and secure important data.
Want to see if you can spot a phish?
Visit the google phishing quiz site.
https://phishingquiz.withgoogle.com/
...
Phishing - From AI Deepfakes to Social Media to QR Code
...
We saw last week that evolving AI has made scams even harder to detect and scammers are always looking for new ways to get your personal information, access to your online accounts, and money. Sometimes they pretend to be your bank or even a member of Suffolk. Sending you a request through email, social media, or even text message. This week we are sticking with Phishing since it is always prevalent and will take another look a AI scams called deepfakes and then a look a some other common phishing attempts such as QR codes and how to report them when they come through email.
(WISH-TV plays on YouTube may have Ads)
Deepfake TIP on how to detect this type of scam
Deepfake scams use artificial intelligence (AI) to create hyper-realistic fake videos, images, and audio that can convincingly impersonate a person.
To spot a deepfake,
- look for visual and audio inconsistencies,
- common scam tactics,
- and always verify unexpected requests through a separate channel.
Below are some great older video with a twist on Shaggy's song "It wasn't me"
If you don't take the time to confirm a request is legitimate you could be giving away your information or money to a scammer.
(Emirates NBD 2019)
Scammers also use are public places to take your personal information and money such as using Fake QR Codes.
Why? Most people are not aware of the risk in QR codes in public places and trust it is associated with that public service. Places like parking meters, parking garages, and even restaurants.
Always verify a QR code before providing any sensitive information when using one. Watch this video from ABC7 Chicago on Fake QR Code TIPS,
(ABC7Chicago plays directly on ABC7 Chicago - may have Ad)
Bottom line for any request is to verify,
If you don't recognize the sender or the message,
- QR - Don't scan the code.
- SMS/Text Message - Don't open the link
- Phone Call - Hang up
Confirm The Source
If you receive a Text Message, Phone Call or QR code from a company you know and trust you should contact them directly to confirm its legitimacy before scanning. For physical QR codes you should check for stickers pasted over a public display.
Spot the phish.
Just like email phishing attempts with be wary of any request via phone, text or QR codes that create a sense of urgency, appeal to your emotions, or have poor grammar.
Review QR code URLs carefully Make sure the URL matches the website you expect to visit before scanning.
Watch out for personal info requests
Don't give out sensitive information, such as login credentials or credit card numbers, to a website you reached through a Email, Text Message or QR code without verify it is legitimate.
Want to see if you can spot a phish?
Visit the google phishing quiz site.
https://phishingquiz.withgoogle.com/
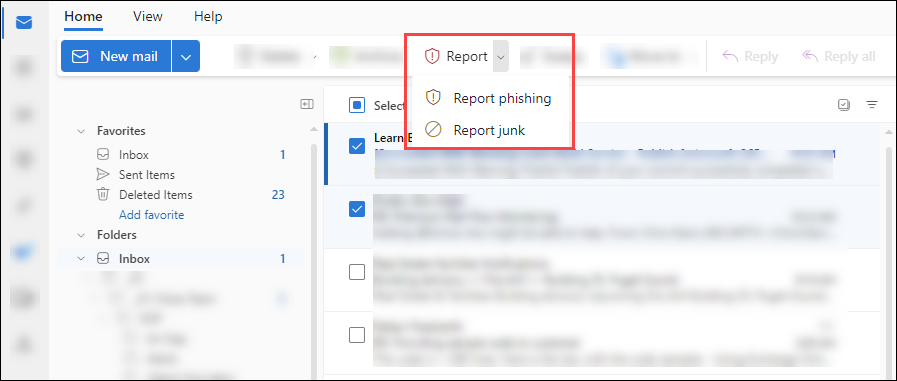
Before you Delete a Phishing Email Message, please Report it using the Report Phishing button in Outlook
How to Report Phishing
Suffolk email filters remove most malicious emails but some get through. This is where we need your help to spot phishing and report it.
What you can do when you know or think an email is phishing is to please report the message in Outlook. Reporting a message as phishing updates our filtering and can potentially protect other users' inboxes from the same or similar message.
To report phishing in Outlook online and desktop Outlook on Windows and Mac.
Select the email you want to report as phishing,
then click the Report button in your toolbar,
then select Report phishing.
(You can find the toolbar directly above your inbox which includes commonly used actions like deleting or marking items as read. See the image below)
Can’t find the report button? Depending on your toolbar’s layout, Report may be hidden under a three-dots menu or dropdown menu. Also note you can customize your toolbar to rearrange your toolbar buttons to make it easier in the future to find.
If you are using Outlook mobile app, tap the three-dots menu at the top of the message. In the dropdown menu, tap “Report” then select “Report Phishing"
What’s the difference between junk and phishing and what happens when I report it?
If you have this question, you’re not alone.
“Junk” is another email word for spam or unsolicited unwanted email. Phishing, on the other hand, is a malicious email meant to steal or trick you into sharing credentials, personal information, installing malicious software, or taking your money.
When you “Report Junk” the message is moved to your Junk Email folder. You still have access to the email and future similar emails are routed to your Junk Email folder.
When you “Report Phishing” Outlook deletes the message from your inbox and it is reported to our Office 365 environment for tuning our filtering potentially new similar bad messages.
...
Phishing and Scams Using AI (Artificial Intelligence)
...
This week we look at how AI is being used to scam you. Phishing doesn't just happen through email, it can be over Text, Phone and even social media. With the evolving AI scammers are making it harder for you to detect these scams. Watch this NBC news video (2022) and see how easy it is to clone someone's voice of a family member, a friend, a co-worker, or even your boss. Pay attention to the things that you can do before you get scammed out of your money or personal information.
Tips to prevent being scammed by AI phishing:
DO
- Pay attention - Be skeptical of any request for money or personal information. With AI anyone's voice can be mimicked easily.
- Confirm. Do not be fooled. Stop and Verify. Always confirm by calling the person back on a known number.
- Safe word - Pause for a second and ask a personal question that person would know. What did you have for dinner? Or something that happened the last time you saw them. For family members it could be setting up a secret word or phrase they can use when in distress.
Now for the DON'Ts
- Do not trust caller id number it can be spoofed. This is true for Text messages, Phone calls.
- Do not trust any request for money, gift cards or personal information.
- Do not be rushed or feel pressured. If you do it is likely a scam.
Phishing Scams that come over text can look like this using AI to create better sounding text messages. Do not be fooled.
Some tips on AI Text Scams
Urgent or Threatening Requests: Be skeptical, scammers use urgency to pressure you into giving personal information, buying gift cards, or even sending money.
Unsolicited Requests: Legitimate organizations do not request sensitive information via text messages. Such as unexpected job offers, internships, fines to be paid, or requesting credentials for user accounts.
Suspicious Links: Just as we saw with QR codes, refrain from clicking on links within text messages unless you have confirmed the link is legitimate. Instead, visit the website directly and log in from there.
Don't Respond: Unsure, Do not reply to the message or engage with the sender in any way. If you think the message is legitimate, always confirm by calling the person directly on a known number. For links go directly to their official web site and do not use the link in the text message.
...
Magic Words and Passwords
...
We start the month with a look at how Passwords are similar to Magic Words (by Wizer), and having a single Magic Word/Password to open everything is not a good idea.
(this video plays directly on the wizer website)
Now that you have seen what having one "Magic Word" for all your accounts can do. Choosing and not sharing your "Magic Word" or Password is just as important.
Hope you have enjoyed the short video and learned that Passwords are like a "Magic Word" and you should make sure that is Strong, Unique, and never share it.
Here are some tips on how to have a strong, unique "Magic Word" and its use.
Having a unique, long, and strong Magic Word (Password) is important. Did you know that a computer can crack an 8-character password in seconds, whereas a 14-character password with complexity (upper and lowercase letters,a number, and a special character) takes centuries to crack? You ask, how can anyone remember a long, complex Magic Word (Password)? Use a Passphrase. A Passphrase is a string of words; it can be as simple as four random words combined to create a memorable Magic Word (Password). Below are tips on how to make it memorable, unique, and strong.
How to create a strong, memorable Magic Word (Password)
Make your passphrase funny so it will be easier to remember (do not use this example as your password)
dogridingsmallbicycle
Now add in complexity (upper and lower case, a number, and a special character)
dog RIDING 24 small bicycles
Great. Now you have a strong, memorable Magic Word (Password).
Keep in mind the following things when creating a Magic Word (Password).
Don't use personal information like your name, birthday, or pet name.
Don't use known phrases from a song, a common saying, or a book. You would need to change part of it to make it unique.
Do use a unique Magic Word (Password) for every login. Have trouble with all those unique Magic Words (Passwords)? Use a password manager to remember all of your Magic Words (Passwords).
If you are reusing Magic Words (Passwords) it is time to stop and update the most sensitive ones first. Like your bank, Suffolk credentials, email, and social media accounts.
Lastly, regardless of how strong your Magic Words (Passwords) are, you should enable Multifactor Authentication (two-factor or 2-step authentication) wherever it is available, so if anyone steals your Magic Word (Password) it will not be enough to log in to your account.
Observed every October, the annual Cyber Security Awareness Month is committed to encouraging personal accountability, secure
The overarching theme for the month is, ‘Do Your Part. #BeCyberSmart.’ and Suffolk University is proud to support this initiative this October.
Throughout the month we will post a new tip or video around the theme of 'Do Your Part. #BeCyberSmart.'
Phishing and Passwords
Phishing is still a common and growing event. Watch this Defense Works sketch where some common phishing scam emails are played out in real life. Maybe after viewing you can better spot phishing scams.
| View file | ||||
|---|---|---|---|---|
|
Phishing attacks use email or malicious websites to get you to respond to steal your personal information or money and can infect your machine with malware and viruses.
Phishing emails may appear to come from a real financial institution, e-commerce site, government agency, or any other service, business, or individual. The email may also request personal information such as account numbers, passwords, or Social Security numbers.
...
- "Are you available? Can you buy me some Gift Cards? I will pay you back"
- "Need a Virtual Assistant. I will send you a Check now... or for the exchange of Gift Cards"
- “We suspect an unauthorized transaction on your account. To ensure that your account is not compromised, please click the link below, and confirm your identity.”
- “During our regular verification of accounts, we couldn’t verify your information. Please click here to update and verify your information.”
- “Our records indicate that your account was overcharged. You must call us within 7 days to receive your refund.”
Passwords. Old but good one. Let's make strong memorable passwords.
| View file | ||||
|---|---|---|---|---|
|
Creating a strong password is an essential step to protecting yourself online and at Suffolk. Using long and complex passwords is one of the easiest ways to defend yourself from cybercrime. Creating a strong password is easier than you think. Follow these simple tips to shake up your password protocol:
...
Use a long passphrase. Consider using the longest password or passphrase permissible. For example, you can use a passphrase such as a news headline or even the title of the last book you read. Then add in some punctuation and capitalization.
Avoid using common words in your password. Substitute letters with numbers and punctuation marks or symbols. For example, @ can replace the letter “A” and an exclamation point (!) can replace the letters “I” or “L.”
Get creative. Use phonetic replacements, such as “PH” instead of “F”. Or make deliberate, but obvious misspellings, such as “enjin” instead of “engine.”
Keep your passwords on the down-low. Don’t tell anyone your passwords and watch for attackers trying to trick you into revealing your passwords through email or calls. Every time you share or reuse a password, it chips away at your security by opening up more avenues in which it could be misused or stolen.
Unique account, unique password. Having different passwords for various accounts helps prevent cybercriminals from gaining access to these accounts and protect you in the event of a breach. It’s important to mix things up—find easy-to-remember ways to customize your standard password for different sites.
Utilize a password manager to remember all your long passwords. The most secure way to store all of your unique passwords is by using a password manager. With just one master password, a computer can generate and retrieve passwords for every account that you have – protecting your online information, including credit card numbers and their three-digit Card Verification Value (CVV) codes, answers to security questions, and more.
For more information on Passwords please visit https://wikis.suffolk.edu/display/ITSEC/Strong+Password
For more information about ways to keep you and your family safe online visit https://staysafeonline.org/stay-safe-online/online-safety-basics/
Observed every October, the annual National Cyber Security Awareness Month (NCSAM) is committed to encouraging personal accountability, securing behaviors, and maintaining digital privacy in the cybersecurity landscape. This initiative was created as a joint effort between government and industry, providing resources to stay safe and secure online.
...